Critical Vulnerabilities discovered from Amazon EKS >>>
Amazon EKS Pod Identity Exposes Credentials
The vulnerability specifically targets Amazon EKS Pod Identity, a feature designed to simplify AWS credential management for pods running in EKS clusters. The service operates through the eks-pod-identity-agent add-on, which runs as a DaemonSet in the kube-system namespace and exposes an API on the link-local address 169.254.170.23 for IPv4 and [fd00:ec2::23] for IPv6 on port 80.
The agent accepts Kubernetes service account tokens in the Authorization header and calls the eks-auth:AssumeRoleForPodIdentity API action.
When applications make AWS service requests, the SDK automatically retrieves temporary credentials from the EKS Pod Identity agent, which then interacts with the AWS API to obtain necessary credentials for the associated IAM role.
Researchers identified two primary attack vectors exploiting excessive container privileges.
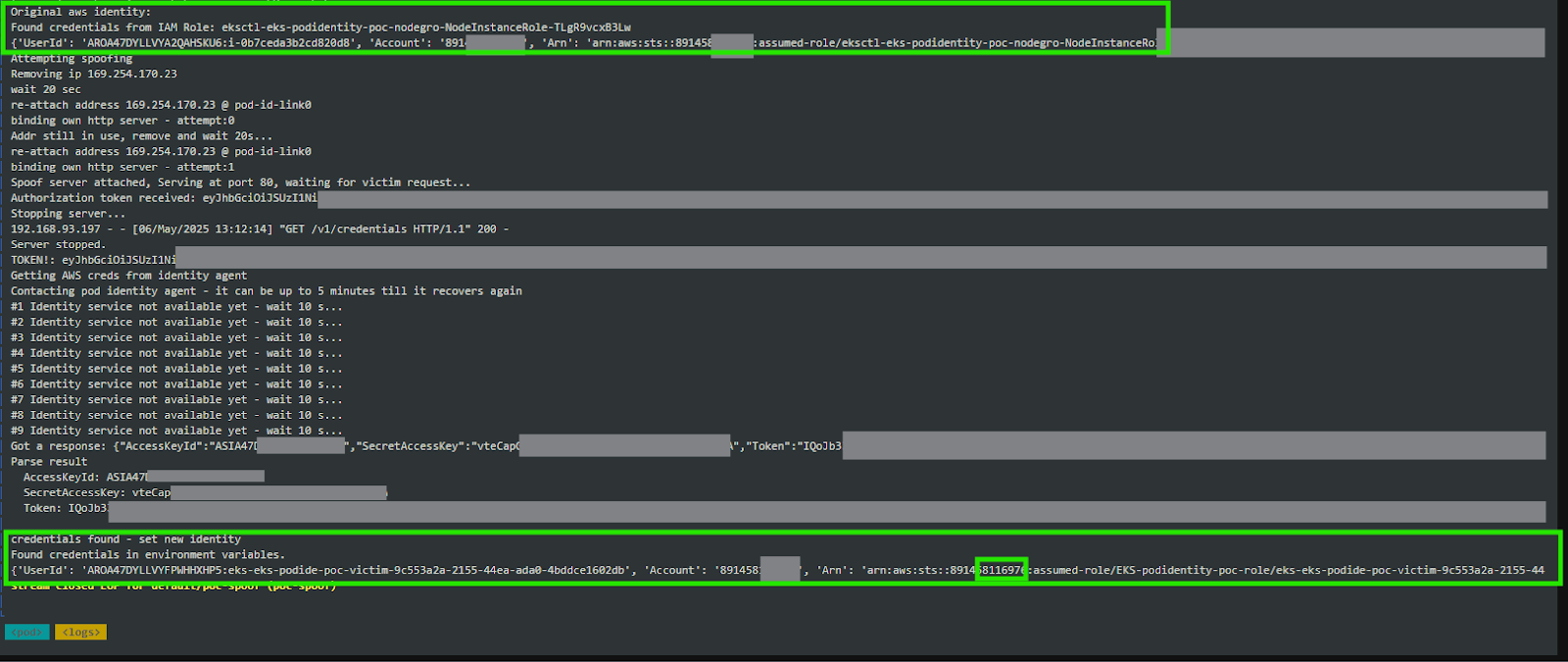
The first involves packet sniffing, where containers configured with hostNetwork: true settings can monitor network traffic and intercept credentials transmitted in plaintext from the API endpoint 169.254.170.23:80.
A proof-of-concept using the standard tcpdump utility successfully demonstrated credential interception in unencrypted HTTP traffic.
The second attack vector employs API spoofing techniques. Even when CAP_NET_RAW capability is removed, containers retaining CAP_NET_ADMIN privileges can manipulate Network Interface Card (NIC) settings.
Attackers can disable the eks-pod-identity-agent HTTP daemon by deleting the local link IP address, then deploy their own HTTP server on 169.254.170.23:80 to intercept Authorization tokens.
Trend Micro developed a Python-based proof-of-concept using the pyroute2 library to demonstrate this exploit.
Mitigation Steps >>
The vulnerabilities were reported to Amazon through the Trend Micro Zero Day Initiative program.
However, AWS determined that this behavior represents expected functionality within the node’s trust boundary and falls under customer responsibility in their shared responsibility model.
To mitigate these risks, organizations should implement the principle of least privilege when configuring containers and utilize security solutions like Trend Vision One Container Security.
The platform can detect and block containers operating with elevated privileges, including those with CAP_NET_RAW, CAP_NET_ADMIN capabilities, or pods with hostNetwork flags set to true.