CVE-2025-22482 and CVE-2025-29892 # QNAP Critical Vulnerabilities >>>
CVE-2025-22482: Format String Exploitation Vulnerability ->
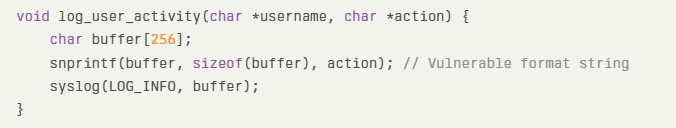
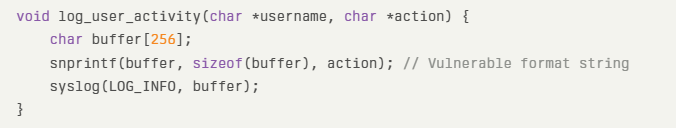
The CVE-2025-22482 vulnerability stems from improper handling of user-supplied format specifiers in C/C++ print-style functions.
The affected code likely contains unprotected calls to functions like sprintf, fprintf, or syslog without proper input validation. Consider this reconstructed vulnerable code snippet:
In this implementation, the action parameter (controlled by an authenticated attacker) contains unescaped format specifiers like %x or %n, enabling memory content disclosure or arbitrary memory writes.
An attacker with valid credentials could:
Use %p specifiers to leak stack pointers and calculate memory offsets.
Employ %s with crafted addresses to read arbitrary memory locations.
Utilize %n to overwrite function pointers or security cookies.
The vulnerability becomes particularly dangerous when combined with other memory corruption flaws, as it potentially enables full Address Space Layout Randomization (ASLR) bypass.
CVE-2025-29892: SQL Injection Vulnerability ->
The CVE-2025-29892 vulnerability exists in Qsync Central’s database abstraction layer.
Examination of the advisory suggests the presence of dynamic SQL construction without proper parameterization. A reconstructed vulnerable code path might appear as:
This implementation allows authenticated attackers to inject SQL commands through the username parameter, bypassing standard authentication checks.
The payload would enumerate database tables, potentially exposing sensitive schema information. More dangerous injections could leverage which would escalate privileges through direct database modification.
The vulnerabilities were responsibly disclosed by security researchers Searat, izut, and coral, highlighting the importance of coordinated vulnerability disclosure in maintaining cybersecurity across enterprise infrastructure platforms.
| CVEs | Affected Products | Impact | Exploit Prerequisites | CVSS 3.1 Score |
| CVE-2025-22482 | Qsync Central 4.5.x | Obtain secret data or modify memory | Attacker must gain access to a user account | 7.8 (High) |
| CVE-2025-29892 | Qsync Central 4.5.x | Execute unauthorized code or commands | Attacker must gain access to a user account | 8.1 (High) |
Mitigations ->
QNAP has already addressed both vulnerabilities in Qsync Central version 4.5.0.6, released on March 20, 2025.
Organizations must immediately update their installations through the QTS or QuTS hero App Center by searching for “Qsync Central” and selecting the Update option.
System administrators should verify that their current version is 4.5.0.6 or later to ensure protection against these vulnerabilities.
Beyond patching, organizations should implement comprehensive security measures, including regular credential audits, multi-factor authentication enforcement, and network segmentation to limit potential attack surfaces.
Security teams should also monitor for unusual access patterns or database queries that might indicate exploitation attempts targeting these vulnerabilities