CVE-2025-23266 and CVE-2025-23267 # NVIDIA Container Toolkit Critical Vulnerabilities >>>
NVIDIA has released critical security updates addressing two significant vulnerabilities in its Container Toolkit and GPU Operator that could allow attackers to execute arbitrary code with elevated permissions.
The vulnerabilities, identified as CVE-2025-23266 and CVE-2025-23267, affect all platforms running NVIDIA Container Toolkit versions up to 1.17.7 and GPU Operator versions up to 25.3.0.
These security flaws pose serious risks including privilege escalation, data tampering, information disclosure, and denial of service attacks.
Critical Container Vulnerabilities >>>
The most severe vulnerability, CVE-2025-23266, carries a CVSS v3.1 base score of 9.0, categorizing it as critical severity.
This vulnerability exists in some hooks used to initialize containers, where an attacker could execute arbitrary code with elevated permissions.
The attack vector is described as “AV:A/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H,” indicating adjacent network access with low attack complexity. The vulnerability is classified under CWE-426, relating to untrusted search path issues.
The second vulnerability, CVE-2025-23267, receives a high severity rating with a CVSS score of 8.5. This flaw affects the update-ldcache hook, where attackers could cause link following attacks using specially crafted container images.
The vulnerability falls under CWE-59, representing improper link resolution before file access.
Both vulnerabilities were discovered through responsible disclosure, with CVE-2025-23266 reported by Nir Ohfeld and Shir Tamari from Trend Zero Day Initiative, and CVE-2025-23267 identified by Lei Wang and Min Yao from Nebula Security Lab at Huawei Cloud.
| CVE ID | Title | Affected Products | CVSS 3.1Score | Severity |
| CVE-2025-23266 | Arbitrary code execution with elevated permissions in container initialization hooks | NVIDIA Container Toolkit (all versions up to 1.17.7)NVIDIA GPU Operator (all versions up to 25.3.0) | 9.0 | Critical |
| CVE-2025-23267 | Link following vulnerability in update-ldcache hook | NVIDIA Container Toolkit (all versions up to 1.17.7)NVIDIA GPU Operator (all versions up to 25.3.0) |
Security Updates >
NVIDIA has released updated versions to address these vulnerabilities. The NVIDIA Container Toolkit requires updating to version 1.17.8 from all previous versions up to 1.17.7.
For the NVIDIA GPU Operator on Linux platforms, users must upgrade to version 25.3.1 from all versions up to 25.3.0. Notably, the CDI mode vulnerability affects only versions prior to 1.17.5 for Container Toolkit and prior to 25.3.0 for GPU Operator.
Organizations can implement immediate mitigations by disabling the vulnerable enable-cuda-compat hook.
For NVIDIA Container Runtime users, this involves editing the /etc/nvidia-container-toolkit/config.toml file and setting the features.disable-cuda-compat-lib-hook feature flag to true: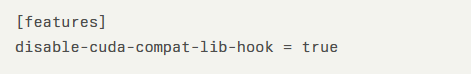 GPU Operator users can apply mitigation through Helm installation arguments:
GPU Operator users can apply mitigation through Helm installation arguments:
 NVIDIA strongly recommends installing the security updates as described in the official NVIDIA Container Toolkit and GPU Operator documentation.
NVIDIA strongly recommends installing the security updates as described in the official NVIDIA Container Toolkit and GPU Operator documentation.