CVE-2025-31644 # F5 BIG-IP Appliance Mode Command Injection Vulnerability POC released >>>
A high-severity vulnerability identified as CVE-2025-31644 has been discovered in F5’s BIG-IP systems operating in Appliance mode, potentially allowing authenticated administrative users to execute arbitrary bash commands and gain root-level access. The flaw was responsibly disclosed by Matei “Mal” Badanoiu of Deloitte and impacts the iControl REST API and the tmsh (Traffic Management Shell) CLI interface.
“A successful exploit can allow the attacker to cross a security boundary,” notes the F5 security advisory.
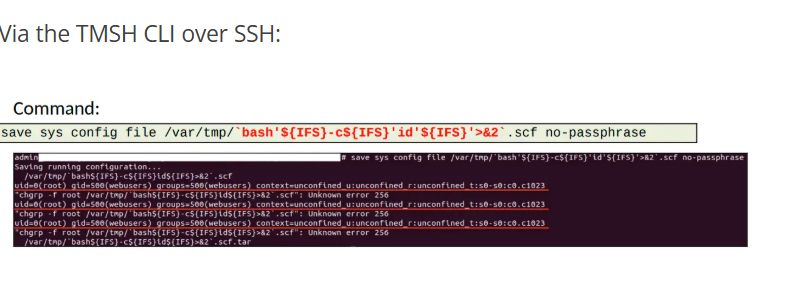
The vulnerability, rated CVSS 8.7 (High), resides in the file parameter of the save command, which is used to store configuration files. This parameter is passed unsafely to underlying Perl scripts or system commands—exposing it to command injection via shell metacharacters, such as backticks (`).
“The ‘file’ parameter of the ‘save’ command is vulnerable to a command injection attack,” the researcher explains, “allowing an authenticated attacker with administrator privileges to… obtain remote code execution as the ‘root’ user.”
Although the save command is broadly accessible, only users with administrator-level privileges can supply custom file paths—an important detail that limits the exploitability but does not diminish the potential impact.
F5 BIG-IP’s Appliance mode is intended to restrict administrative users from accessing the underlying bash shell, enforcing operational separation between the control and data planes. However, this flaw undermines that boundary:
“This may allow an authenticated attacker… to bypass the Appliance mode security that would otherwise prevent the execution of arbitrary Advanced Shell (bash) commands,” the advisory explains.
Crucially, this is not a data plane vulnerability, but a control plane compromise. Still, it can be weaponized to manipulate system-level configurations, plant persistence mechanisms, or pivot to lateral movement in restricted environments.
The vulnerability can be triggered via two primary vectors - Refer to the attached images .
The vulnerability affects the following F5 BIG-IP branches:
| Product Branch | Vulnerable Versions | Fixed in Version |
|---|---|---|
| 17.x | 17.1.0 – 17.1.2 | 17.1.2.2 |
| 16.x | 16.1.0 – 16.1.5 | 16.1.6 |
| 15.x | 15.1.0 – 15.1.10 | 15.1.10.7 |
Organizations running BIG-IP in Appliance mode should immediately apply the vendor patches for the affected versions.