CVE-2025-4978 # NETGEAR Router Critical Vulnerability >>>
A newly disclosed and highly critical vulnerability, tracked as CVE-2025-4978 with a CVSSv4 score of 9.3, has been discovered in the NETGEAR DGND3700v2 router. The vulnerability allows unauthenticated remote attackers to bypass login credentials entirely by exploiting what appears to be an embedded backdoor in the router’s web interface.
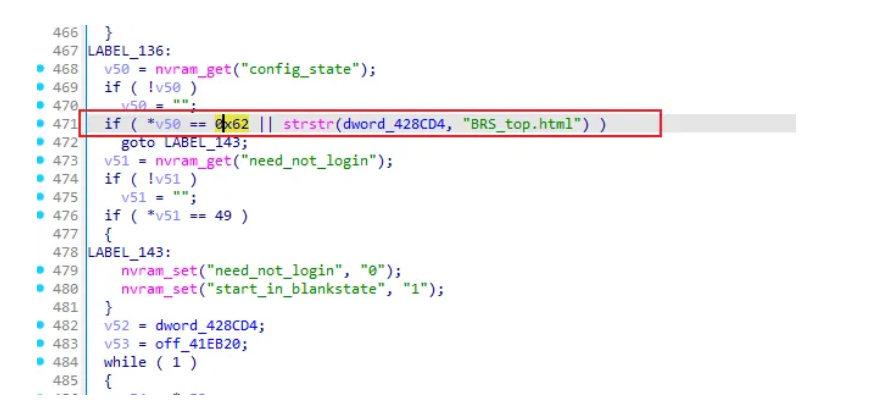
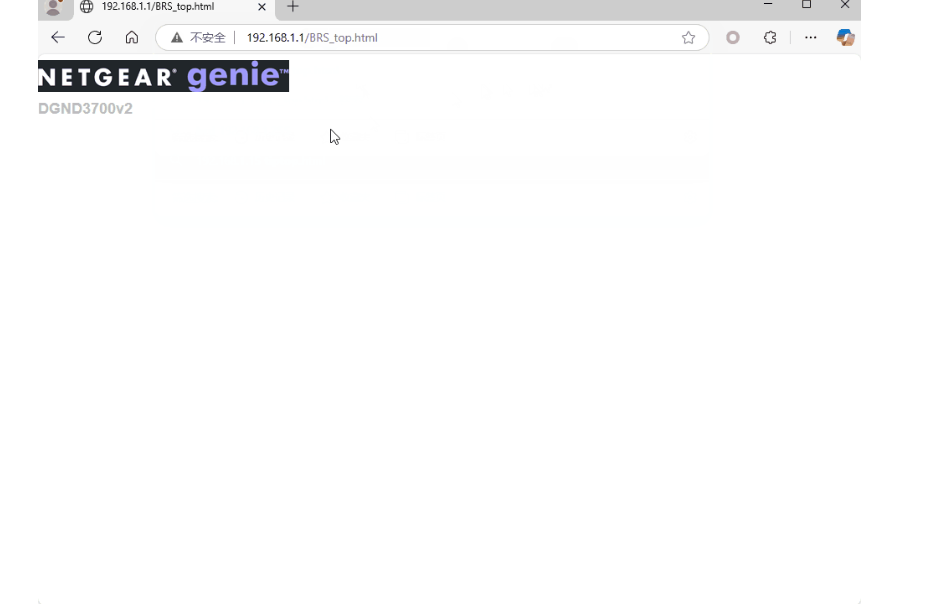
“By accessing the unauthenticated endpoint /BRS_top.html, the internal flag start_in_blankstate is set to 1, which disables HTTP Basic Authentication checks,” explains security researcher at0de, who uncovered the flaw.
The vulnerability exists in the router’s embedded mini_http server, a lightweight HTTP daemon used to serve the device’s administrative interface. A specific endpoint—/BRS_top.html—can be accessed without prior authentication. When triggered, this page sets an internal variable named start_in_blankstate to 1.
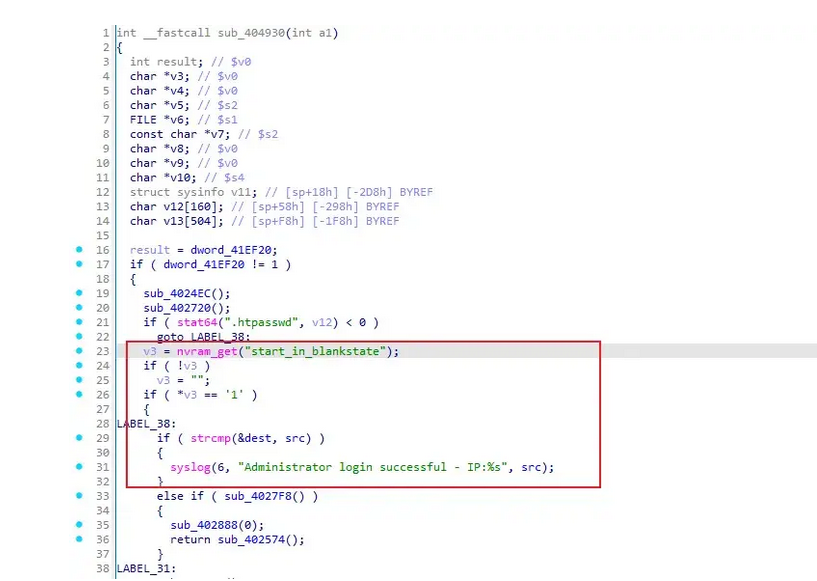
“If start_in_blankstate=1, the verification is skipped, allowing users to access all features without permissions, which appears to be a backdoor,” according to at0de’s technical analysis.
This flag is later used in a function responsible for processing authentication logic (sub_404930). When the flag is active, the HTTP Basic Authentication check is entirely bypassed. This behavior effectively opens the door for attackers to gain full access to the router’s configuration interface—including network settings, credentials, firewall configurations, and potentially stored VPN or Wi-Fi details—without needing a username or password.
This flaw affects NETGEAR DGND3700v2 running firmware version V1.1.00.15_1.00.15NA. The implications of CVE-2025-4978 are severe. Anyone with access to the router’s administrative interface—such as from a local network or if remote management is enabled—can take control of the device in seconds.
Attackers could:
Change DNS settings for traffic redirection
Install persistent malware
Harvest credentials from connected devices
Disable security features such as firewalls or parental controls
Because the exploit is incredibly simple to trigger and requires no authentication, it poses a major risk to home users and small businesses alike.
NETGEAR releases firmware version 1.1.00.26 to patch this flaw.