Microsoft Entra ID Vulnerability Overview #
A critical vulnerability in Microsoft Entra ID allows attackers to escalate privileges to the Global Administrator role through the exploitation of first-party applications.
The vulnerability, reported to Microsoft Security Response Center (MSRC) in January 2025, affects organizations using hybrid Active Directory environments with federated domains.
Microsoft Entra ID Vulnerability >>>
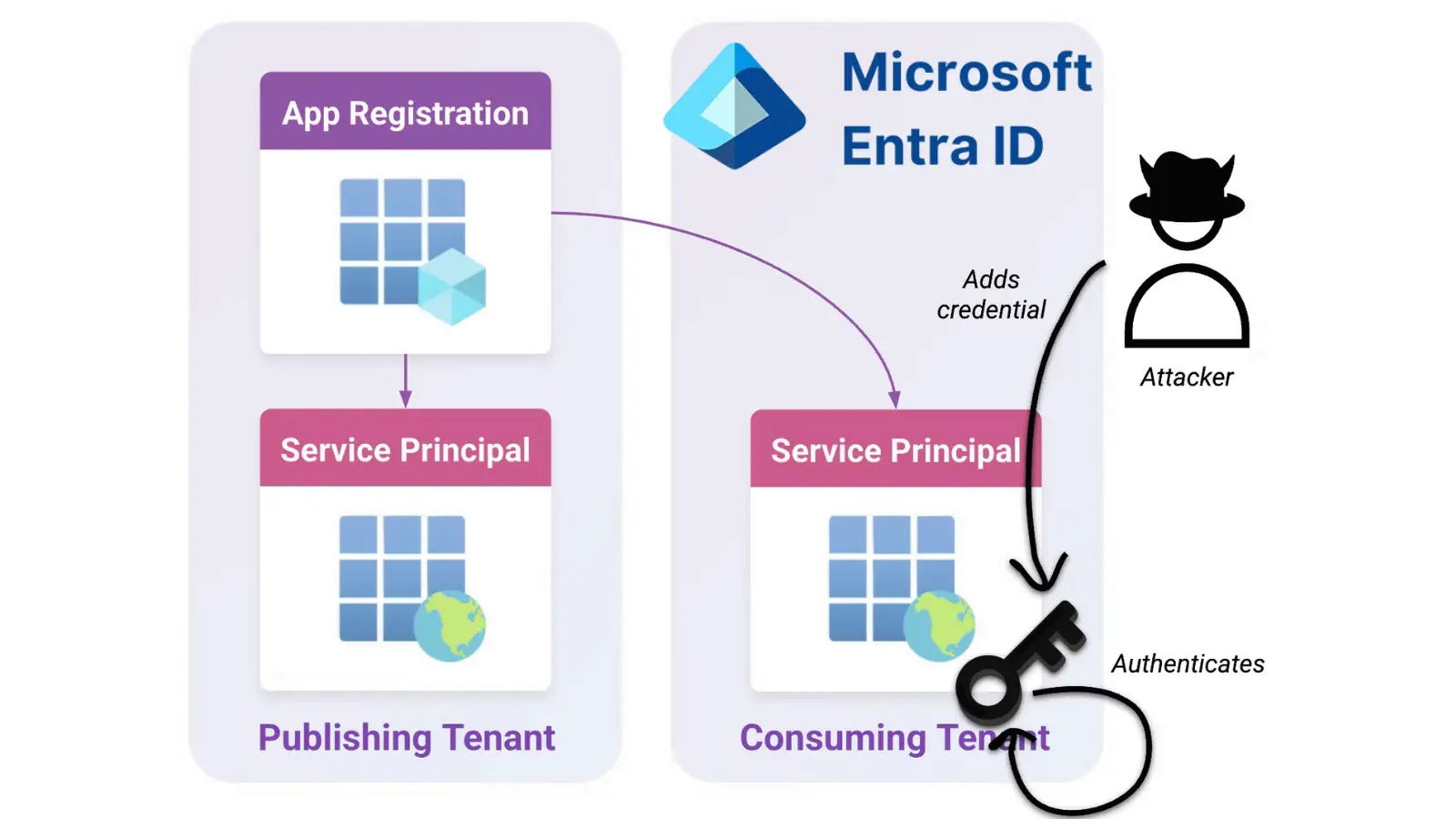
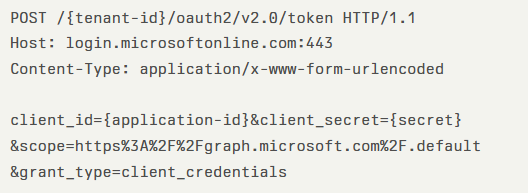
Security researchers at Datadog discovered that service principals (SPs) assigned the Cloud Application Administrator role, Application Administrator role, or Application.ReadWrite.All permission can escalate their privileges by hijacking the built-in Office 365 Exchange Online service principal (Client ID: 00000002-0000-0ff1-ce00-000000000000).
The vulnerability works by exploiting the Office 365 Exchange Online SP’s Domain.ReadWrite.All permission to add a new federated domain to the tenant.
Attackers can then forge SAML tokens as any hybrid tenant user synchronized between on-premises Active Directory (AD) and Entra ID, including users with Global Administrator privileges.
Federated Domain Backdoor Technique
The privilege escalation follows a five-step process involving federated domain manipulation.
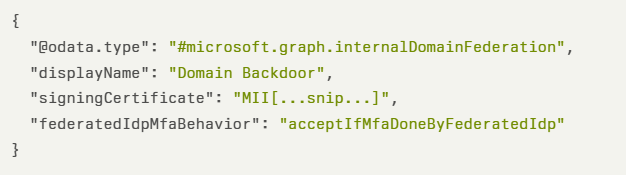
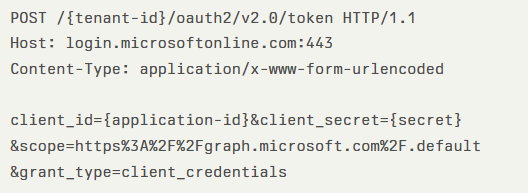
Attackers first add a malicious domain using the Microsoft Graph API endpoint POST /v1.0/domains, then verify it through DNS records.
This configuration allows attackers to forge SAML tokens with MFA claims, bypassing multi-factor authentication requirements while maintaining the appearance of legitimate authentication in sign-in logs.
Microsoft’s Response >>>
Datadog reported this vulnerability to the Microsoft Security Response Center (MSRC) on January 14, 2025, initiating a months-long disclosure process.
However, on May 14, 2025, MSRC concluded that this “is not a security vulnerability but expected behavior of the Application Administrator role and its associated permissions”.
Microsoft’s response emphasized that the scenario reflects misconfiguration rather than a security bypass, stating that Application Administrator roles inherently include the ability to manage application credentials and impersonate application identities.