Security Post-Exploitation Toolkit For Active Directory Reconnaissance & Exploitation >>>
Toolkit Name - Cable
Security researchers and penetration testers have a powerful new tool in their arsenal with the recent development of Cable, an advanced post-exploitation toolkit designed specifically for Active Directory environments.
Created by developer Logan Goins, this .NET-based utility provides comprehensive capabilities for reconnaissance and exploitation of Discretionary Access Control List (DACL) vulnerabilities within enterprise networks.
Cable operates as a modular command-line tool that enables security professionals to thoroughly assess Active Directory security postures after initial access has been achieved.
The toolkit, which saw significant updates as recently as yesterday, focuses on identifying and exploiting permission-based vulnerabilities that could allow attackers to escalate privileges or maintain persistence within compromised networks.
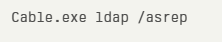
The primary command syntax follows a straightforward structure:
Where modules include specialized functions for different aspects of Active Directory assessment.
Key Modules and FunctionsCable’s architecture is divided into nine core modules, each targeting specific Active Directory attack vectors:
ldap: Performs comprehensive enumeration of Active Directory objects, including users, computers, groups, and service accounts with configurable search filtersdclist: Identifies all Domain Controllers in the current domainrbcd: Manipulates the msDs-AllowedToActOnBehalfOfOtherIdentity attribute for Resource-Based Constrained Delegation attacksdacl: Reads or modifies Access Control Entries (ACEs) on objectstrusts: Maps domain and forest trust relationshipsca: Discovers Active Directory Certificate Services (ADCS) certificate authoritiestemplates: Assesses potentially vulnerable certificate templatesuser: Performs operations on user accounts, including SPN manipulation and password resetscomputer: Adds or removes computer accounts from the domaingroup: Manages group membership and enumerates users within groups
Technical ImplementationSecurity researchers can leverage Cable for targeted reconnaissance with commands like:
This identifies accounts configured without Kerberos pre-authentication requirements, potentially vulnerable to ASREProast attacks.
For DACL manipulation, the toolkit offers precise control:
This command grants full control permissions to a specified account, demonstrating the tool’s capability to exploit misconfigured access controls.
According to the project documentation, Cable was “primarily created to learn more about .NET offensive development in an Active Directory context.”
The developer notes that the tool serves both as a learning project and as a means to expand knowledge of “Active Directory focused offensive security”.
The toolkit is published under the GPL-3.0 license, making it freely available for security professionals to use in authorized penetration testing and security assessment activities.
While Cable provides valuable functionality for legitimate security testing, its capabilities also underscore the importance of properly securing Active Directory environments.
Organizations should regularly audit their Active Directory permissions, implement the principle of least privilege, and monitor for unauthorized DACL modifications.
The tool’s recent updates included improvements to computer account source display functionality, indicating ongoing development and refinement of its capabilities.
For security teams conducting authorized assessments, Cable represents a significant addition to the Active Directory testing toolkit, offering a comprehensive suite of reconnaissance and exploitation modules in a single, well-documented framework.