ZDI-CAN-25373 # Zero-Day Vulnerability
A sophisticated cyber espionage campaign attributed to the XDSpy threat actor has recently been discovered exploiting a zero-day vulnerability in Windows shortcut files.
This threat actor, which has operated largely undetected from 2011 until its initial discovery in 2020, has primarily targeted government entities in Eastern Europe and Russia, showing no links to known APT groups in code, infrastructure, or targeting patterns.
The attack leverages a vulnerability dubbed “ZDI-CAN-25373,” which enables attackers to hide executed commands from the Windows user interface in specially crafted shortcut files.
First reported by Trend Micro in March 2025, this vulnerability allows malicious actors to pad command line arguments with whitespace characters, effectively rendering them invisible in the Windows LNK properties dialog while still executing the hidden commands when triggered.
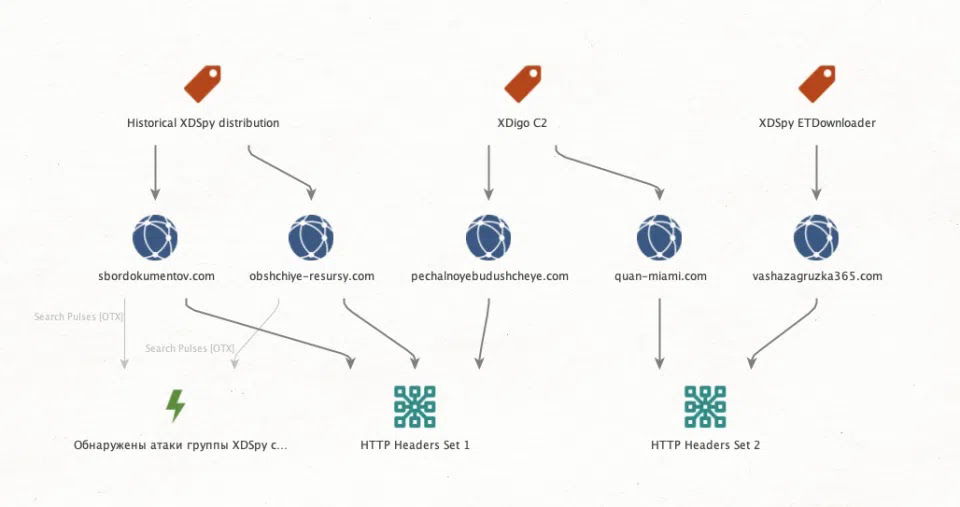
HarfangLab researchers identified a cluster of malicious LNK files in mid-March that exploited this vulnerability as part of a coordinated campaign.
Their investigation revealed not only the exploitation of ZDI-CAN-25373 but also a deeper issue in how Windows parses LNK files differently from its own MS-SHLLINK specification, creating an additional confusion vector that malicious actors can leverage to further obfuscate their attacks.
The campaign primarily targeted Russian-speaking recipients, with decoy documents discovered during analysis including a scan of a document addressed to the President of the Presidium in Kazakhstan’s Almaty City Bar Association and a floor map with network and electricity installation plans from a Moscow architectural design firm.
This indicates XDSpy’s continued focus on government and infrastructure targets in Eastern Europe.
Infection Mechanism ->
The infection chain begins with the victim receiving a ZIP archive (named either dokazatelstva.zip or proyekt.zip) containing a malicious LNK file and another ZIP disguised with an .ini extension.
When the user opens the LNK file, it triggers an intricate Windows shell command one-liner designed to unpack and execute the malicious components while displaying a decoy document to the victim.
The LNK file leverages both the ZDI-CAN-25373 vulnerability and the LNK parsing confusion to hide its true intentions. A simplified version of the Windows shell command contained in the LNK file demonstrates its complexity:-
set PATH=%windir%\system32;%PATH% & ( chcp 65001 | echo | set /p="import System; import System.IO; import System.IO.Compression; [...truncated JavaScript .NET code...] Main();" > %TEMP%\B5DUC80ULT7L.a [...more code to compile and execute...] )
This command extracts and executes a first-stage malware dubbed “ETDownloader,” a .NET DLL which is sideloaded by a legitimate signed Microsoft executable.
ETDownloader establishes persistence by creating a startup batch file and attempts to download a second-stage payload called “XDigo” from a command and control server using hardcoded URLs.
The XDigo implant, written in Go, contains sophisticated data collection capabilities designed to evade analysis and steal sensitive information.
It performs regular scans for documents with specific extensions, captures screenshots, monitors clipboard content, and has command execution capabilities, all while employing encryption for data exfiltration.
This campaign represents a significant evolution in XDSpy’s tactics, combining zero-day exploitation with sophisticated multi-stage payloads, demonstrating that this previously low-profile threat actor continues to develop advanced capabilities for targeted cyber espionage operations.